The Global Zero Trust Architecture Market size was valued at USD 18.7 Billion in 2024 and is projected to reach USD 84.2 Billion by 2033 at a CAGR of around 18.2% between 2024 and 2033. The global Zero Trust Architecture (ZTA) market is driven by increasing cyber threats and the rapid shift to cloud-based environments. Ransomware attacks and data breaches have surged, forcing enterprises to adopt ZTA for enhanced security. Cloud adoption has grown, requiring strict access controls to prevent unauthorized access. However, implementation complexity acts as a major restraint. Businesses struggle with integrating ZTA into legacy systems, delaying adoption. Despite this, two key opportunities exist. First, the rise of remote work has increased demand for secure network access.
Companies deploy Zero Trust solutions to protect remote employees from phishing and credential theft. Second, government regulations mandate stronger cybersecurity measures. Financial institutions adopt ZTA to secure online banking and digital transactions. Healthcare providers implement it to protect patient records from cyberattacks. Retailers use Zero Trust frameworks to safeguard customer payment data. Manufacturing firms secure IoT-connected devices to prevent operational disruptions. Cloud service providers enhance security by offering built-in Zero Trust solutions. AI-driven threat detection further strengthens ZTA adoption across industries. As digital transformation accelerates, Zero Trust remains critical in mitigating cyber risks. Businesses invest in identity verification, continuous monitoring, and micro-segmentation to protect sensitive data and maintain compliance with evolving security standards.

Driver: Rising Cyber Threats Driving ZTA Adoption
The surge in cyber threats has made Zero Trust Architecture (ZTA) a necessity for businesses. Traditional security models fail to prevent sophisticated attacks, leading organizations to adopt a “never trust, always verify” approach. Cybercriminals target enterprises with ransomware, disrupting operations and demanding hefty payouts. Large corporations have faced supply chain attacks, where hackers exploit third-party vendors to gain access to sensitive systems. Banks implement Zero Trust to secure financial transactions from credential theft and account takeovers. E-commerce platforms rely on it to prevent fraud and unauthorized access to customer data. Healthcare providers use ZTA to safeguard electronic medical records from ransomware attacks that could compromise patient care. Government agencies strengthen national security by applying Zero Trust principles to protect classified information from cyber espionage. Manufacturing firms secure industrial control systems from cyber intrusions that could halt production. Educational institutions implement strict authentication measures to protect student and faculty data from phishing attempts. Cloud service providers integrate ZTA frameworks to ensure data integrity and prevent unauthorized access. As cyber threats evolve, businesses across industries prioritize Zero Trust to mitigate risks. Continuous verification, identity-based access, and real-time monitoring remain critical in defending against modern cyberattacks.
Key Insights:
- The adoption rate of Zero Trust principles among global enterprises has surpassed 50%.
- A leading technology company invested over USD 1 billion in Zero Trust security initiatives in the last fiscal year.
- Government agencies in the United States allocated USD 500 million for Zero Trust implementation in 2024.
- Over 10 million Zero Trust-enabled devices were deployed globally in 2023.
- The penetration rate of Zero Trust solutions in the financial services sector reached 70%.
- The healthcare industry reported a 60% adoption rate of Zero Trust frameworks for securing patient data.
- A major telecommunications provider implemented Zero Trust across its network, covering over 5 million endpoints.
- The education sector saw a 40% integration of Zero Trust strategies to protect sensitive academic and administrative data.
Segment Analysis:
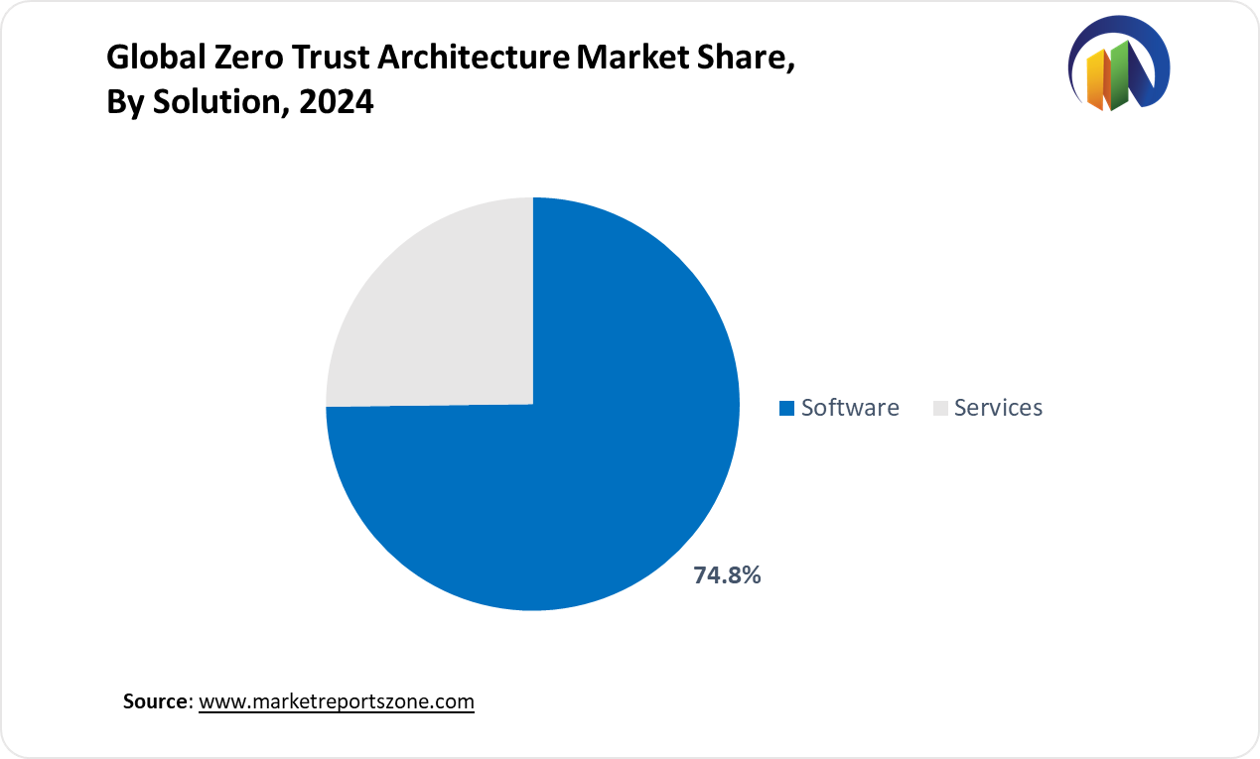
The Zero Trust Architecture (ZTA) market spans multiple segments, shaping security strategies across industries. Software solutions dominate, with enterprises deploying identity management and micro-segmentation tools to restrict unauthorized access. Services, including consulting and managed security, help businesses transition smoothly. On-premise deployment remains crucial for government agencies securing classified data, while cloud-based models gain traction among e-commerce firms handling high-traffic transactions. Large enterprises invest in advanced ZTA frameworks to prevent insider threats, whereas SMEs adopt cost-effective, cloud-driven solutions for data protection. In applications, network security plays a key role, with telecom companies using Zero Trust to secure 5G infrastructure. Data security adoption grows as financial institutions protect sensitive banking information from cyber fraud. Endpoint security remains vital, with remote workforces requiring device authentication to prevent breaches. Cloud security strengthens as SaaS providers ensure multi-layered defense for hosted applications. Application security sees increased demand, with online gaming platforms using Zero Trust to prevent account takeovers. In end-use industries, healthcare firms deploy ZTA to secure telemedicine platforms, and retailers implement strict authentication for digital payments. Government agencies enhance cybersecurity resilience against nation-state attacks. As cyber threats intensify, Zero Trust adoption continues expanding, ensuring proactive security measures for evolving digital ecosystems.
Regional Analysis:
The Zero Trust Architecture (ZTA) market is expanding across regions as organizations prioritize cybersecurity. In North America, strict data protection laws drive ZTA adoption, with financial institutions securing mobile banking applications from credential theft. Large tech firms deploy Zero Trust to protect AI-driven data centers from insider threats. Europe sees rising demand due to stringent compliance regulations, with pharmaceutical companies using ZTA to safeguard clinical trial data. Automotive manufacturers integrate Zero Trust to prevent cyber intrusions in connected vehicle systems. The Asia-Pacific region experiences rapid growth as businesses digitize operations. E-commerce giants deploy Zero Trust frameworks to secure millions of daily transactions, while telecom firms use it to prevent SIM swap fraud. Latin America witnesses increased adoption as digital banking expands, with fintech startups using ZTA to counter identity theft. Retailers secure customer loyalty programs from account takeovers. In the Middle East & Africa, government initiatives push Zero Trust adoption for national security. Oil and gas companies secure industrial networks from cyber threats targeting critical infrastructure. Cloud providers invest in Zero Trust solutions to support enterprise clients. As cyber risks grow, organizations worldwide implement Zero Trust strategies to ensure continuous monitoring, identity verification, and secure data access across industries.
Competitive Scenario:
Leading cybersecurity companies are expanding their Zero Trust Architecture (ZTA) solutions to counter rising cyber threats. Microsoft has integrated Zero Trust into its cloud security offerings, enabling enterprises to enforce strict identity verification. Palo Alto Networks has introduced AI-powered Zero Trust solutions to detect anomalies and prevent unauthorized access in real-time. Cisco has enhanced its Zero Trust framework by incorporating network segmentation and multi-factor authentication to secure hybrid work environments. IBM focuses on Zero Trust for critical infrastructure, helping industries like finance and healthcare protect sensitive data. Cloudflare has strengthened its Zero Trust platform by improving secure access controls for remote workers. Okta has expanded its identity and access management (IAM) solutions to support Zero Trust authentication, reducing the risk of credential theft. Check Point has developed advanced endpoint security tools to complement Zero Trust strategies for businesses with distributed networks. Fortinet has integrated Zero Trust principles into its Secure Access Service Edge (SASE) solutions to improve enterprise security. CyberArk is helping financial institutions secure privileged accounts using Zero Trust methodologies. As cyber risks grow, companies continue investing in Zero Trust innovations, ensuring secure authentication, real-time monitoring, and enhanced data protection for organizations across industries.
Zero Trust Architecture Market Report Scope
| Report Attribute | Details |
|---|
| Market Size Value in 2024 | USD 18.7 Billion |
| Revenue Forecast in 2033 | USD 84.2 Billion |
| Growth Rate | CAGR of 18.2% from 2025 to 2033 |
| Historic Period | 2021 - 2024 |
| Forecasted Period | 2025 - 2033 |
| Report Coverage | Revenue forecast, company ranking, competitive landscape, growth factors, and trends |
| Regions Covered | North America; Europe; Asia Pacific; Latin America; Middle East & Africa |
| Countries Covered | U.S.; Canada; Mexico, UK; Germany; France; Spain; Italy; Russia; China; Japan; India; South Korea; Australia; Southeast Asia; Brazil; Argentina; Saudi Arabia; UAE; South Africa |
| Key companies profiled | Akamai Technologies, Inc.; Check Point Software Technologies Ltd.; Cisco Systems, Inc.; Citrix; Cloud Strike; Cloudflare; CyberArk Software Ltd.; Forcepoint, LLC; Fortinet; IBM Corporation; Microsoft Corporation; Netskope, Inc.; Okta, Inc.; Palo Alto Networks, Inc.; Proofpoint, Inc.; SailPoint Technologies, Inc.; Trellix; Others |
| Customization | Free report customization (equivalent up to 8 analysts working days) with purchase. Addition or alteration to country, regional & segment scope. |
The Global Zero Trust Architecture Market report is segmented as follows:
By Solution,
By Deployment,
By Enterprise Size,
By Application,
- Network Security
- Data Security
- Endpoint Security
- Cloud Security
- Application Security
By End User,
- BFSI
- Healthcare
- IT and Telecom
- Government and Defense
- Retail & E-commerce
- Others
By Region,
- North America
- Europe
- UK
- Germany
- France
- Spain
- Italy
- Russia
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Australia
- Southeast Asia
- Rest of Asia Pacific
- Latin America
- Brazil
- Argentina
- Rest of Latin America
- Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Rest of Middle East & Africa
Key Market Players,
- Akamai Technologies, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Citrix
- Cloud Strike
- Cloudflare
- CyberArk Software Ltd.
- Forcepoint, LLC
- Fortinet
- IBM Corporation
- Microsoft Corporation
- Netskope, Inc.
- Okta, Inc.
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- SailPoint Technologies, Inc.
- Trellix
- Others
Frequently Asked Questions
The Global Zero Trust Architecture Market was valued at USD 18.7 Billion in 2024 and is projected to reach USD 84.2 Billion by 2033.
The Global Zero Trust Architecture Market is expected to grow at a CAGR of 18.2% during the forecasted period.
The North America holds the largest market share in the global Zero Trust Architecture Market in 2024.
Key players profiled in the global Zero Trust Architecture market are Akamai Technologies, Inc.; Check Point Software Technologies Ltd.; Cisco Systems, Inc.; Citrix; Cloud Strike; Cloudflare; CyberArk Software Ltd.; Forcepoint, LLC; Fortinet; IBM Corporation; Microsoft Corporation; Netskope, Inc.; Okta, Inc.; Palo Alto Networks, Inc.; Proofpoint, Inc.; SailPoint Technologies, Inc.; Trellix; Others.
Research Objectives
- Proliferation and maturation of trade in the global Zero Trust Architecture Market .
- The market share of the global Zero Trust Architecture Market , supply and demand ratio, growth revenue, supply chain analysis, and business overview.
- Current and future market trends that are influencing the growth opportunities and growth rate of the global Zero Trust Architecture Market .
- Feasibility study, new market insights, company profiles, investment return, market size of the global Zero Trust Architecture Market .
Chapter 1 Zero Trust Architecture Market Executive Summary
- 1.1 Zero Trust Architecture Market Research Scope
- 1.2 Zero Trust Architecture Market Estimates and Forecast (2021-2033)
- 1.2.1 Global Zero Trust Architecture Market Value and Growth Rate (2021-2033)
- 1.2.2 Global Zero Trust Architecture Market Price Trend (2021-2033)
- 1.3 Global Zero Trust Architecture Market Value Comparison, by Solution (2021-2033)
- 1.3.1 Software
- 1.3.2 Services
- 1.4 Global Zero Trust Architecture Market Value Comparison, by Deployment (2021-2033)
- 1.4.1 On-premise
- 1.4.2 Cloud based
- 1.5 Global Zero Trust Architecture Market Value Comparison, by Enterprise Size (2021-2033)
- 1.5.1 SME
- 1.5.2 Large Enterprises
- 1.6 Global Zero Trust Architecture Market Value Comparison, by Application (2021-2033)
- 1.6.1 Network Security
- 1.6.2 Data Security
- 1.6.3 Endpoint Security
- 1.6.4 Cloud Security
- 1.6.5 Application Security
- 1.7 Global Zero Trust Architecture Market Value Comparison, by End User (2021-2033)
- 1.7.1 BFSI
- 1.7.2 Healthcare
- 1.7.3 IT and Telecom
- 1.7.4 Government and Defense
- 1.7.5 Retail & E-commerce
- 1.7.6 Others
Chapter 2 Research Methodology
- 2.1 Introduction
- 2.2 Data Capture Sources
- 2.2.1 Primary Sources
- 2.2.2 Secondary Sources
- 2.3 Market Size Estimation
- 2.4 Market Forecast
- 2.5 Assumptions and Limitations
Chapter 3 Market Dynamics
- 3.1 Market Trends
- 3.2 Opportunities and Drivers
- 3.3 Challenges
- 3.4 Market Restraints
- 3.5 Porter's Five Forces Analysis
Chapter 4 Supply Chain Analysis and Marketing Channels
- 4.1 Zero Trust Architecture Supply Chain Analysis
- 4.2 Marketing Channels
- 4.3 Zero Trust Architecture Suppliers List
- 4.4 Zero Trust Architecture Distributors List
- 4.5 Zero Trust Architecture Customers
Chapter 5 COVID-19 & Russia–Ukraine War Impact Analysis
- 5.1 COVID-19 Impact Analysis on Zero Trust Architecture Market
- 5.2 Russia-Ukraine War Impact Analysis on Zero Trust Architecture Market
Chapter 6 Zero Trust Architecture Market Estimate and Forecast by Region
- 6.1 Global Zero Trust Architecture Market Value by Region: 2021 VS 2023 VS 2033
- 6.2 Global Zero Trust Architecture Market Scenario by Region (2021-2023)
- 6.2.1 Global Zero Trust Architecture Market Value Share by Region (2021-2023)
- 6.3 Global Zero Trust Architecture Market Forecast by Region (2024-2033)
- 6.3.1 Global Zero Trust Architecture Market Value Forecast by Region (2024-2033)
- 6.4 Geographic Market Analysis: Market Facts and Figures
- 6.4.1 North America Zero Trust Architecture Market Estimates and Projections (2021-2033)
- 6.4.2 Europe Zero Trust Architecture Market Estimates and Projections (2021-2033)
- 6.4.3 Asia Pacific Zero Trust Architecture Market Estimates and Projections (2021-2033)
- 6.4.4 Latin America Zero Trust Architecture Market Estimates and Projections (2021-2033)
- 6.4.5 Middle East & Africa Zero Trust Architecture Market Estimates and Projections (2021-2033)
Chapter 7 Global Zero Trust Architecture Competition Landscape by Players
- 7.1 Global Top Zero Trust Architecture Players by Value (2021-2023)
- 7.2 Zero Trust Architecture Headquarters and Sales Region by Company
- 7.3 Company Recent Developments, Mergers & Acquisitions, and Expansion Plans
Chapter 8 Global Zero Trust Architecture Market, by Solution
- 8.1 Global Zero Trust Architecture Market Value, by Solution (2021-2033)
- 8.1.1 Software
- 8.1.2 Services
Chapter 9 Global Zero Trust Architecture Market, by Deployment
- 9.1 Global Zero Trust Architecture Market Value, by Deployment (2021-2033)
- 9.1.1 On-premise
- 9.1.2 Cloud based
Chapter 10 Global Zero Trust Architecture Market, by Enterprise Size
- 10.1 Global Zero Trust Architecture Market Value, by Enterprise Size (2021-2033)
- 10.1.1 SME
- 10.1.2 Large Enterprises
Chapter 11 Global Zero Trust Architecture Market, by Application
- 11.1 Global Zero Trust Architecture Market Value, by Application (2021-2033)
- 11.1.1 Network Security
- 11.1.2 Data Security
- 11.1.3 Endpoint Security
- 11.1.4 Cloud Security
- 11.1.5 Application Security
Chapter 12 Global Zero Trust Architecture Market, by End User
- 12.1 Global Zero Trust Architecture Market Value, by End User (2021-2033)
- 12.1.1 BFSI
- 12.1.2 Healthcare
- 12.1.3 IT and Telecom
- 12.1.4 Government and Defense
- 12.1.5 Retail & E-commerce
- 12.1.6 Others
Chapter 13 North America Zero Trust Architecture Market
- 13.1 Overview
- 13.2 North America Zero Trust Architecture Market Value, by Country (2021-2033)
- 13.2.1 U.S.
- 13.2.2 Canada
- 13.2.3 Mexico
- 13.3 North America Zero Trust Architecture Market Value, by Solution (2021-2033)
- 13.3.1 Software
- 13.3.2 Services
- 13.4 North America Zero Trust Architecture Market Value, by Deployment (2021-2033)
- 13.4.1 On-premise
- 13.4.2 Cloud based
- 13.5 North America Zero Trust Architecture Market Value, by Enterprise Size (2021-2033)
- 13.5.1 SME
- 13.5.2 Large Enterprises
- 13.6 North America Zero Trust Architecture Market Value, by Application (2021-2033)
- 13.6.1 Network Security
- 13.6.2 Data Security
- 13.6.3 Endpoint Security
- 13.6.4 Cloud Security
- 13.6.5 Application Security
- 13.7 North America Zero Trust Architecture Market Value, by End User (2021-2033)
- 13.7.1 BFSI
- 13.7.2 Healthcare
- 13.7.3 IT and Telecom
- 13.7.4 Government and Defense
- 13.7.5 Retail & E-commerce
- 13.7.6 Others
Chapter 14 Europe Zero Trust Architecture Market
- 14.1 Overview
- 14.2 Europe Zero Trust Architecture Market Value, by Country (2021-2033)
- 14.2.1 UK
- 14.2.2 Germany
- 14.2.3 France
- 14.2.4 Spain
- 14.2.5 Italy
- 14.2.6 Russia
- 14.2.7 Rest of Europe
- 14.3 Europe Zero Trust Architecture Market Value, by Solution (2021-2033)
- 14.3.1 Software
- 14.3.2 Services
- 14.4 Europe Zero Trust Architecture Market Value, by Deployment (2021-2033)
- 14.4.1 On-premise
- 14.4.2 Cloud based
- 14.5 Europe Zero Trust Architecture Market Value, by Enterprise Size (2021-2033)
- 14.5.1 SME
- 14.5.2 Large Enterprises
- 14.6 Europe Zero Trust Architecture Market Value, by Application (2021-2033)
- 14.6.1 Network Security
- 14.6.2 Data Security
- 14.6.3 Endpoint Security
- 14.6.4 Cloud Security
- 14.6.5 Application Security
- 14.7 Europe Zero Trust Architecture Market Value, by End User (2021-2033)
- 14.7.1 BFSI
- 14.7.2 Healthcare
- 14.7.3 IT and Telecom
- 14.7.4 Government and Defense
- 14.7.5 Retail & E-commerce
- 14.7.6 Others
Chapter 15 Asia Pacific Zero Trust Architecture Market
- 15.1 Overview
- 15.2 Asia Pacific Zero Trust Architecture Market Value, by Country (2021-2033)
- 15.2.1 China
- 15.2.2 Japan
- 15.2.3 India
- 15.2.4 South Korea
- 15.2.5 Australia
- 15.2.6 Southeast Asia
- 15.2.7 Rest of Asia Pacific
- 15.3 Asia Pacific Zero Trust Architecture Market Value, by Solution (2021-2033)
- 15.3.1 Software
- 15.3.2 Services
- 15.4 Asia Pacific Zero Trust Architecture Market Value, by Deployment (2021-2033)
- 15.4.1 On-premise
- 15.4.2 Cloud based
- 15.5 Asia Pacific Zero Trust Architecture Market Value, by Enterprise Size (2021-2033)
- 15.5.1 SME
- 15.5.2 Large Enterprises
- 15.6 Asia Pacific Zero Trust Architecture Market Value, by Application (2021-2033)
- 15.6.1 Network Security
- 15.6.2 Data Security
- 15.6.3 Endpoint Security
- 15.6.4 Cloud Security
- 15.6.5 Application Security
- 15.7 Asia Pacific Zero Trust Architecture Market Value, by End User (2021-2033)
- 15.7.1 BFSI
- 15.7.2 Healthcare
- 15.7.3 IT and Telecom
- 15.7.4 Government and Defense
- 15.7.5 Retail & E-commerce
- 15.7.6 Others
Chapter 16 Latin America Zero Trust Architecture Market
- 16.1 Overview
- 16.2 Latin America Zero Trust Architecture Market Value, by Country (2021-2033)
- 16.2.1 Brazil
- 16.2.2 Argentina
- 16.2.3 Rest of Latin America
- 16.3 Latin America Zero Trust Architecture Market Value, by Solution (2021-2033)
- 16.3.1 Software
- 16.3.2 Services
- 16.4 Latin America Zero Trust Architecture Market Value, by Deployment (2021-2033)
- 16.4.1 On-premise
- 16.4.2 Cloud based
- 16.5 Latin America Zero Trust Architecture Market Value, by Enterprise Size (2021-2033)
- 16.5.1 SME
- 16.5.2 Large Enterprises
- 16.6 Latin America Zero Trust Architecture Market Value, by Application (2021-2033)
- 16.6.1 Network Security
- 16.6.2 Data Security
- 16.6.3 Endpoint Security
- 16.6.4 Cloud Security
- 16.6.5 Application Security
- 16.7 Latin America Zero Trust Architecture Market Value, by End User (2021-2033)
- 16.7.1 BFSI
- 16.7.2 Healthcare
- 16.7.3 IT and Telecom
- 16.7.4 Government and Defense
- 16.7.5 Retail & E-commerce
- 16.7.6 Others
Chapter 17 Middle East & Africa Zero Trust Architecture Market
- 17.1 Overview
- 17.2 Middle East & Africa Zero Trust Architecture Market Value, by Country (2021-2033)
- 17.2.1 Saudi Arabia
- 17.2.2 UAE
- 17.2.3 South Africa
- 17.2.4 Rest of Middle East & Africa
- 17.3 Middle East & Africa Zero Trust Architecture Market Value, by Solution (2021-2033)
- 17.3.1 Software
- 17.3.2 Services
- 17.4 Middle East & Africa Zero Trust Architecture Market Value, by Deployment (2021-2033)
- 17.4.1 On-premise
- 17.4.2 Cloud based
- 17.5 Middle East & Africa Zero Trust Architecture Market Value, by Enterprise Size (2021-2033)
- 17.5.1 SME
- 17.5.2 Large Enterprises
- 17.6 Middle East & Africa Zero Trust Architecture Market Value, by Application (2021-2033)
- 17.6.1 Network Security
- 17.6.2 Data Security
- 17.6.3 Endpoint Security
- 17.6.4 Cloud Security
- 17.6.5 Application Security
- 17.7 Middle East & Africa Zero Trust Architecture Market Value, by End User (2021-2033)
- 17.7.1 BFSI
- 17.7.2 Healthcare
- 17.7.3 IT and Telecom
- 17.7.4 Government and Defense
- 17.7.5 Retail & E-commerce
- 17.7.6 Others
Chapter 18 Company Profiles and Market Share Analysis: (Business Overview, Market Share Analysis, Products/Services Offered, Recent Developments)
- 18.1 Akamai Technologies, Inc.
- 18.2 Check Point Software Technologies Ltd.
- 18.3 Cisco Systems, Inc.
- 18.4 Citrix
- 18.5 Cloud Strike
- 18.6 Cloudflare
- 18.7 CyberArk Software Ltd.
- 18.8 Forcepoint, LLC
- 18.9 Fortinet
- 18.10 IBM Corporation
- 18.11 Microsoft Corporation
- 18.12 Netskope, Inc.
- 18.13 Okta, Inc.
- 18.14 Palo Alto Networks, Inc.
- 18.15 Proofpoint, Inc.
- 18.16 SailPoint Technologies, Inc.
- 18.17 Trellix
- 18.18 Others




